Risk management is a key element of security standards and regulations because it enables organizations to identify, assess, and mitigate potential threats that could compromise their information systems and data. For example, ISO-27001 requires organizations to identify security risks, assess their likelihood and impact, and implement measures to manage them, including regular review and updates. Similarly, the NIST RMF involves categorizing systems, selecting and implementing security controls, regularly assessing these controls, and continuous monitoring. SOC 2, which focuses on data management for cloud service providers, requires identifying and managing risks related to security, availability, and processing integrity of data. HIPAA, which protects health information, and PCI/DSS, which focuses on payment card security, have similar risk management requirements. The Cybersecurity Act establishes a framework for protecting critical information infrastructure and requires organizations to implement measures to identify, assess, and mitigate cyber risks.
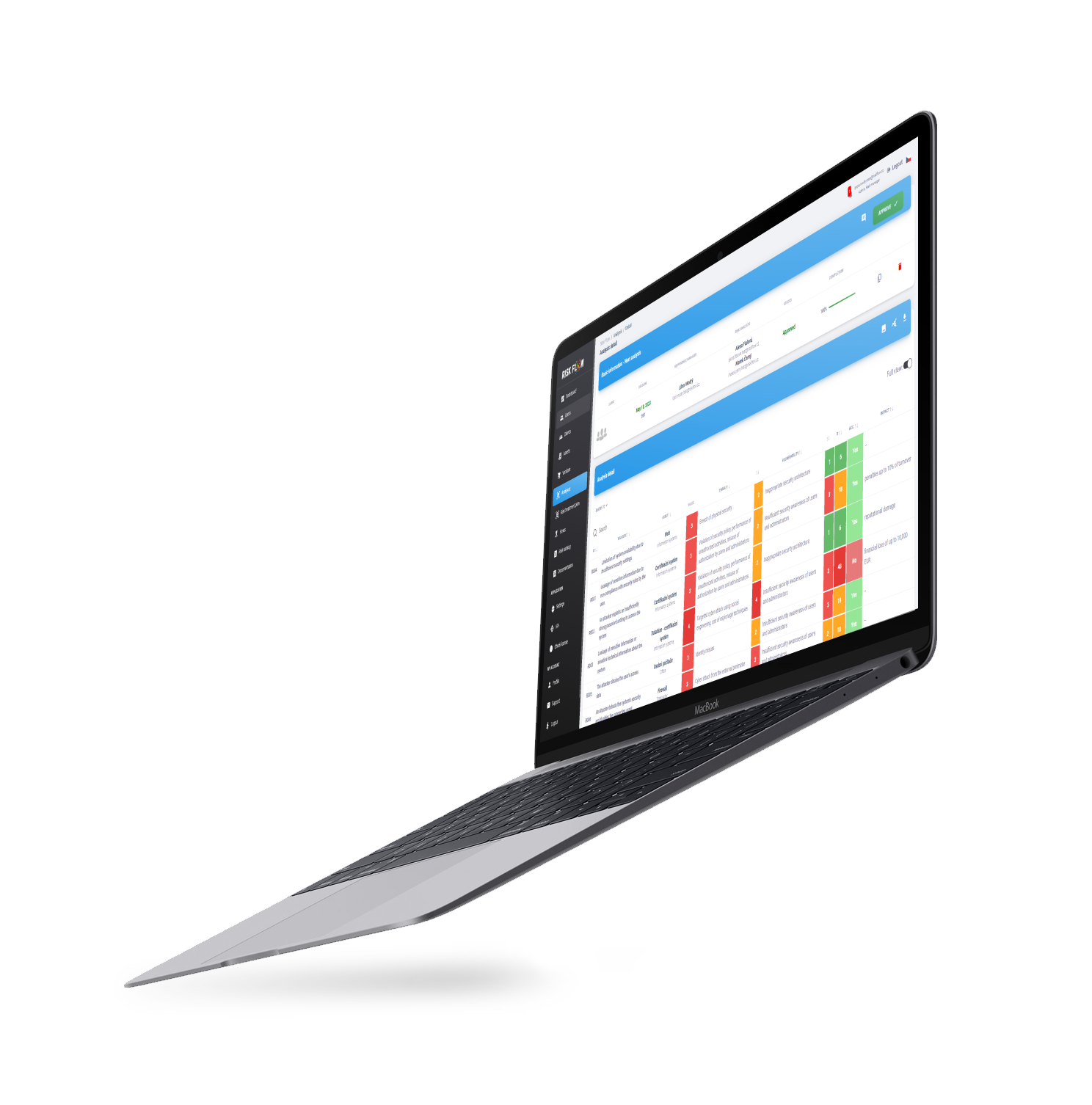
Risk Flow is a very suitable helper when analyzing the risks of the IT environment. Keep control of the organization's assets. With Risk Flow, the whole team can work efficiently on analyses, and with flow management, you have control over all approval processes!
Risk Flow can be run on its own infrastructure and thus have control over all parts of the system and stored data. We will also be happy to offer you the opportunity to operate 100% in our cloud and take care of infrastructure management for you. This means you can choose between full control over your system and data within your own infrastructure or the convenience and simplicity of management offered by our cloud solution. In both cases, we ensure a high level of security and reliability, so you can be sure that your data and processes are in good hands. If you choose the cloud option, our team of experts will take care of all technical aspects, including updates, maintenance and backups, allowing you to focus on your core business activities without having to invest in your own IT infrastructure.
We try to create a pleasant and user-friendly environment. Our main goal is to make it easier for analysts and managers to perform risk analysis.
The system is suitable for any large company or organization that has some IT assets and wants (or must) regularly evaluate risks, threats, vulnerabilities and their possible impact. Regardless of business size or industry, this system provides tools for comprehensive risk analysis and management, enabling organizations to effectively identify potential threats and implement appropriate mitigation measures. The system supports scalability, so it is equally effective for small businesses and large corporations with extensive IT infrastructures.
We use an artificial intelligence module that can be completely isolated from the Internet during On-Premise installations. In this way, you can use the full potential of artificial intelligence integration and at the same time be sure that no third party has access to your data. This module offers advanced analytical capabilities, which significantly increases the efficiency and accuracy of risk management and other critical operations. This setup allows you to have full control over your data and ensures that sensitive information remains secure within your infrastructure, which is especially important for organizations with high demands on security and data protection. It is also possible to connect Risk Flow to third-party systems, such as Open AI.